With access to sensitive data and digital assets, banking and finance employees sit at the frontlines of social engineering attacks, making them high-value targets for increasingly sophisticated, AI-powered schemes.
Social engineering (SE) attacks are a type of cyberattack that relies on manipulating human psychology to achieve malicious purposes against digital systems. It generally aims to steal sensitive data, account credentials or to manipulate target personnel to grant access to protected system resources.
Following the public release of ChatGPT in late 2022, SE attacks have become more sophisticated as cybercriminals began leveraging artificial intelligence (AI) technology in their attack strategies. For instance, SlashNext's report "State of Phishing" reveals a 1,265% increase in phishing emails since the launch of ChatGPT, which signals the emergence of a new era in cyber attacks boosted by generative AI technology.
SE represents a major threat to both organizations and individuals. For instance, it is estimated that 90% of all successful cyber-attacks begin with email phishing. Business email compromise (BEC), a type of SE attack that does not require installing malware, cost the world 50 billion between 2013 and 2023, according to the FBI. At the same time, the Verizon 2024 Data Breach Investigations Report states that 68% of breaches involved a non-malicious human element, such as falling victim to an SE attack. The previous figures make understanding and mitigating SE attacks a top priority for incident response teams and IT leaders worldwide.
Common SE attacks targeting banking employees
Banking and finance employees are prime targets for SE attacks. Financial organizations are particularly attractive to cybercriminals because they hold both sensitive customer information and substantial monetary assets. Attackers target not only finance employees but also their customers, including banking and insurance company clients, to gain unauthorized access to their digital funds.
While there are numerous types of social engineering attacks, we will focus on the four most prevalent methods targeting finance employees:
Phishing
Phishing is a type of SE attack that commonly exploits email to steal target sensitive information, such as private banking data, account credentials or tricks users into installing data-stealing malware, such as keylogger, on their computing device.
The email poses as legitimate correspondence from trusted financial institutions. In banking operations, attackers craft emails appearing to originate from the victim's bank, asking for urgent password resets or account verification to keep the online account active (see Figure 1). When targeting banking personnel, these deceptive emails often impersonate internal IT department teams, executive leadership, high-value clients or financial regulators, like SEC and Federal Reserve. These attacks frequently involve sophisticated replicas of internal banking portals and confidential document requests. Attackers exploit financial deadlines, audit periods or market volatility to create urgency in their demands, often requesting immediate wire transfers or sensitive customer information through targeted spear-phishing campaigns.
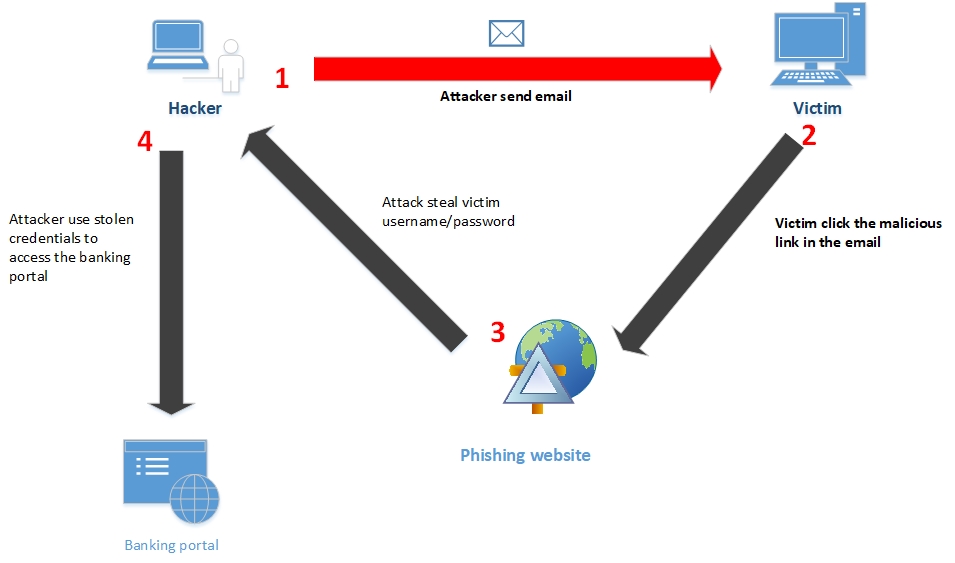
Figure 1 - How phishing email works
Spear phishing
Spear phishing is a highly targeted form of phishing that focuses on specific individuals or organizations. Unlike generic phishing campaigns, attackers use open-source intelligence techniques (OSINT) to gather detailed background information about their targets. For instance, they may research publicly available data about a bank's IT department, including employee names, roles and internal processes. Equipped with this information, they craft convincing emails that appear to originate from the IT department and target employees in other departments, such as finance and senior management. These emails often contain urgent requests or malicious links, which exploit the trust between internal teams in the financial institution.
Whaling
While spear phishing targets specific groups or individuals, whaling attacks focus on high-level executives in the finance and banking sector, such as CEOs, CFOs, or board chairpersons. Whaling, also known as CEO fraud, involves threat actors investing substantial time in gathering intelligence about their targets using OSINT techniques.
Threat actors research the target organization's business operations and examine executives' digital footprints across social media platforms and other public sources, such as email aggregators and government databases. Their objective is to craft persuasive emails that replicate authentic business communications. These emails employ accurate language that matches the executive's communication writing style and tone.
For banking personnel, these messages typically originate from what appears to be the CEO or senior leadership, requesting time-sensitive actions such as:
- Authorizing emergency wire transfers to close a strategic partnership or a major deal
- Request access to restricted financial IT systems
- Releasing confidential business partners and acquisition details
- Bypassing standard security protocols for "critical" or high-value transactions
The high-level authority of the supposed sender often convinces employees to execute these requests without proper verification. This makes whaling attacks a very dangerous threat in the financial operations arenas. The attack's sophistication and precise targeting make it particularly challenging to identify and counter efficiently.
Business Email Compromise (BEC)
BEC shares similar tactics with whaling attacks but employs a different social engineering vector. For instance, rather than targeting C-suite executives directly, attackers impersonate them. The attack chain typically begins with reconnaissance to map organizational hierarchies and financial workflows. Attackers gather executive details - writing style, signature, out-of-office schedules – using OSINT techniques to craft convincing impersonation emails.
A notable example of BEC is the attack against the Kentucky city in 2022, which resulted in losing $4 million in federal funding intended for housing assistance after an attacker successfully transferred it to their private bank account instead of sending it to the nonprofit Community Action Council.
The primary attack vector leverages organizational power hierarchy: lower-level employees, particularly those in the finance department, face implicit pressure to rapidly execute requests from senior leadership. Attackers exploit this fact by fabricating urgent wire transfer requests that appear to come from legitimate executive accounts.
Common BEC techniques include:
- CEO Fraud — Attackers impersonate high-level executives (e.g., CEO, CFO) and request lower-level employees to transfer funds urgently
- Vendor impersonation — Criminals pose as trusted vendors or suppliers and request payment for fake invoices. An example of such an attack is receiving an email to the finance department from a fake email pretending to be one of your suppliers to change bank details. "Our bank details have changed. Please send the next payment to this new account."
- Account compromise — Threat actors gain illegal access to one of the senior management emails and use it to send fraudulent requests to initiate money transfers. For example, a finance worker receives an email from their boss requesting to transfer 50000 USD to close an urgent deal
As we note, BEC exploits trust and urgency to manipulate victims into complying with the attacker's objectives. Learn more about business email compromise techniques in detail in our BEC blog.
Deepfake attacks
While not traditionally classified within social engineering attack taxonomies, deepfake-based attacks have emerged as a sophisticated threat vector, particularly in the financial sector. The proliferation of accessible neural network architectures and ML frameworks has lowered the technical barrier to creating synthetic media.
Deepfake attacks use AI-generated audio, video or images to impersonate someone in a way that looks completely identical. In the banking and finance sector, the attack works by using AI and ML to create fake audio or video of a high-level executive (e.g., CEO, CFO) or a trusted client/vendor to manipulate employees into executing unauthorized actions, such as transferring funds or sharing sensitive work information. Learn more about how to verify against deepfake attacks.
How does it work in social engineering?
SE attacks rely on psychological manipulation to exploit human trust and bypass traditional security measures. Deepfakes amplify this by adding a layer of realism that makes deception harder for humans to detect. For example:
Audio deepfakes — A banking employee receives a phone call from what sounds like their CFO, urgently asking them to transfer funds to a private bank account controlled by the attacker. One of the first attacks using this technique was executed in 2019 when criminals used AI-based software to impersonate a CEO and demand a fraudulent transfer of €220,000 ($243,000).
Video deepfakes — A fake video of a client or executive is used in a virtual meeting to authorize a high-value transaction. In a notable 2024 incident, threat actors leveraged synthetic video generation to impersonate a CFO during a video conference session. The attack chain involved:
- High-fidelity facial mapping of the target executive
- Real-time video synthesis during the conference call
- Voice pattern replication matching the CFO's speech characteristics
The attackers successfully manipulated a finance department employee into authorizing a $25 million wire transfer by exploiting both technical and psychological vectors. This incident clearly demonstrates how AI technology can bypass traditional video-based verification protocols in corporate environments to execute SE attacks.
Why deepfake attacks are dangerous for banking employees
Different reasons make deepfake attacks dangerous for finance and banking employees:
- Exploit trust: Finance employees are trained to trust communications from executives or high-valued clients. Deepfakes exploit this trust by mimicking voices or appearances with high accuracy
- Using urgent language: Attackers often create a sense of urgency, pressuring employees to act quickly without verifying the request. For example, they use the following urgent phrases to press on recipients:
- Invoking CEO authority with phrases like "immediate attention required."
- Creating fabricated deadlines to force immediate decisions. For example, "The deal should be closed by tomorrow morning".
- Threatening negative business impacts for delays. For example, "Failing to close the deal could result in big financial penalties and damage to the company's reputation."
- Bypassing traditional security: Deepfakes can circumvent standard email or phone verification automated detection solutions, as they appear to come from legitimate sources
Social engineering attacks targeting the financial and banking sectors have evolved rapidly, particularly after the widespread availability of AI technologies. The major attack vectors — phishing, spear phishing, whaling, BEC and deepfake attacks — exploit human psychology and organizational hierarchies to bypass technical security controls. The financial impact is important, and integrating security solutions with end user training becomes critical to halt such attacks.
SOC, CSIRT and IS teams need a way to rapidly triage and remediate suspected phishing and other social engineering attacks. For safe and compliant access, SOC teams at Fortune 500s rely on Silo: the digital investigations platform to securely conduct, anonymize, manage and track incident response investigations.
Tags Phishing/malware SOC

